General Settings consists of all the details about the fetched data. You can find the most recent attempt made to fetch data in Last Fetch Attempt and the last date and time when data was successfully fetched in Last Fetch Date. The information of a disabled Threat Intelligence source is not displayed.
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select Logpoint to view the details about the fetched data. You can select multiple Logpoints of different pools.
Select General Settings from the Select Plugin Sub-type drop-down.
Click NEXT.
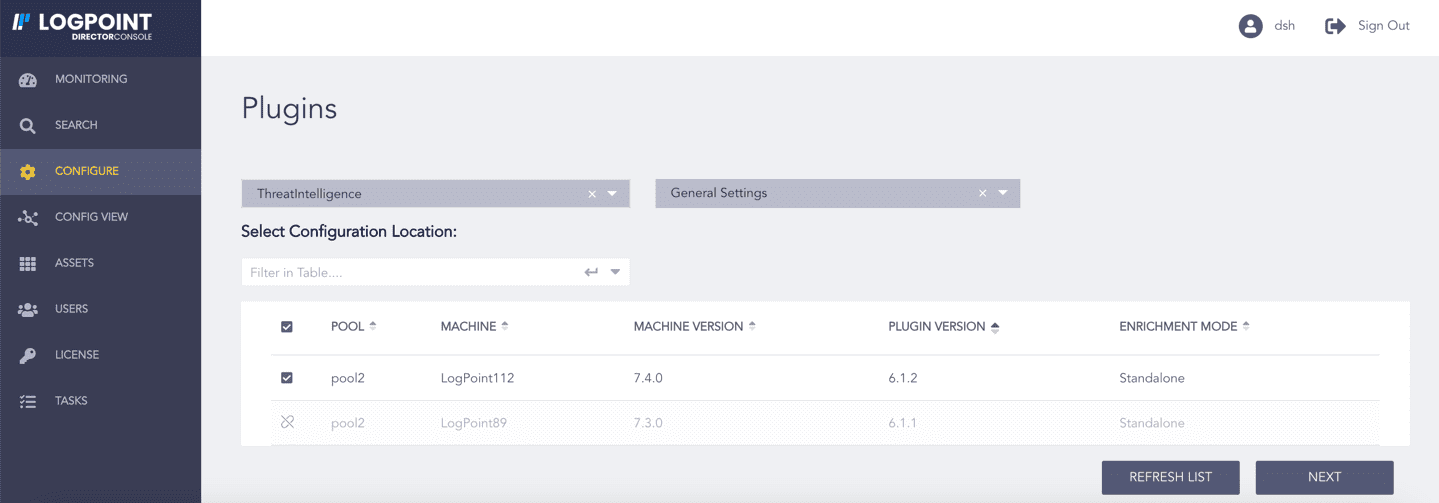
Selecting General Settings¶
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select a Logpoint to configure Emerging Threats. You can select multiple Logpoints of different pools.
Select Emerging Threats from the Select Plugin Sub-type drop-down.
Click NEXT.
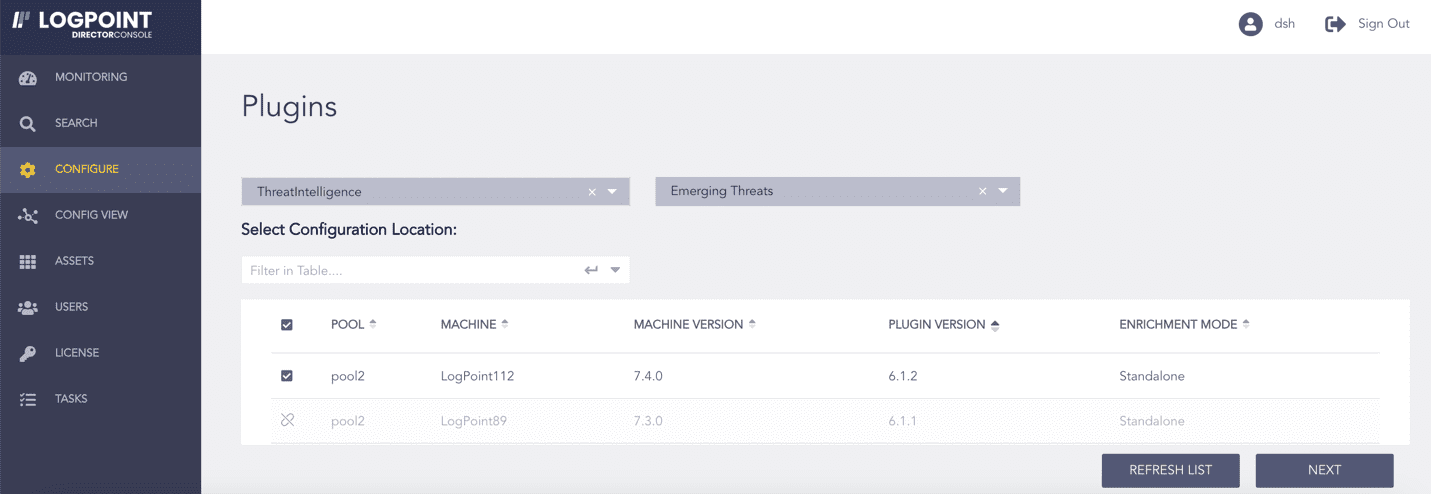
Selecting Emerging Threats¶
Select Enable Source to activate Emerging Threats.
Enter the Emerging Threats Base URL and API Key. In API Key, you must enter the API generated after you configure the required feeds of Threat Intelligence data on Emerging Threat.
Enter the Fetch Interval.
Select the Fetch Interval Unit in hours or days.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select the Age Limit Unit in hours or days.
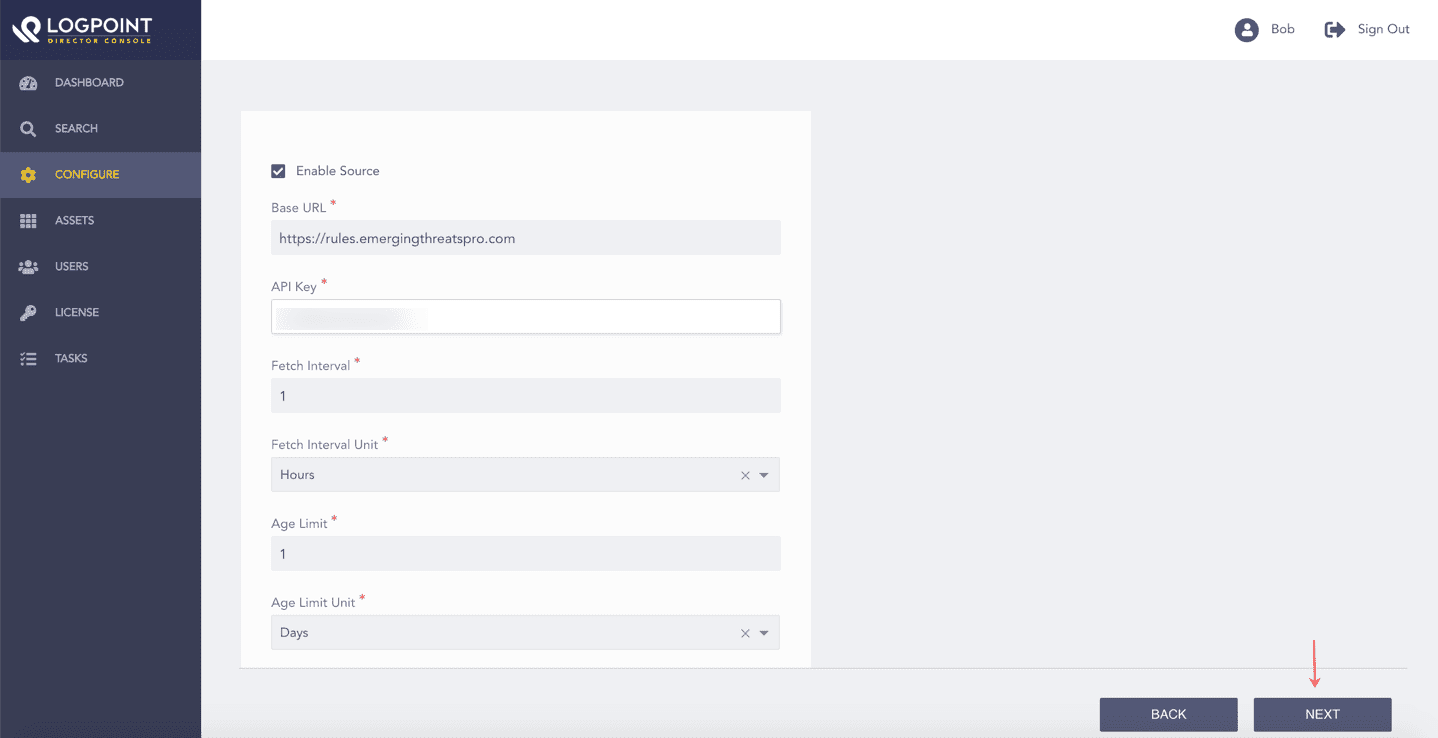
Enabling Emerging Threats¶
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
14.1. Enter the proxy server IP Address and Port number.
14.2. Select the Http or Https protocol as required.
Click NEXT.
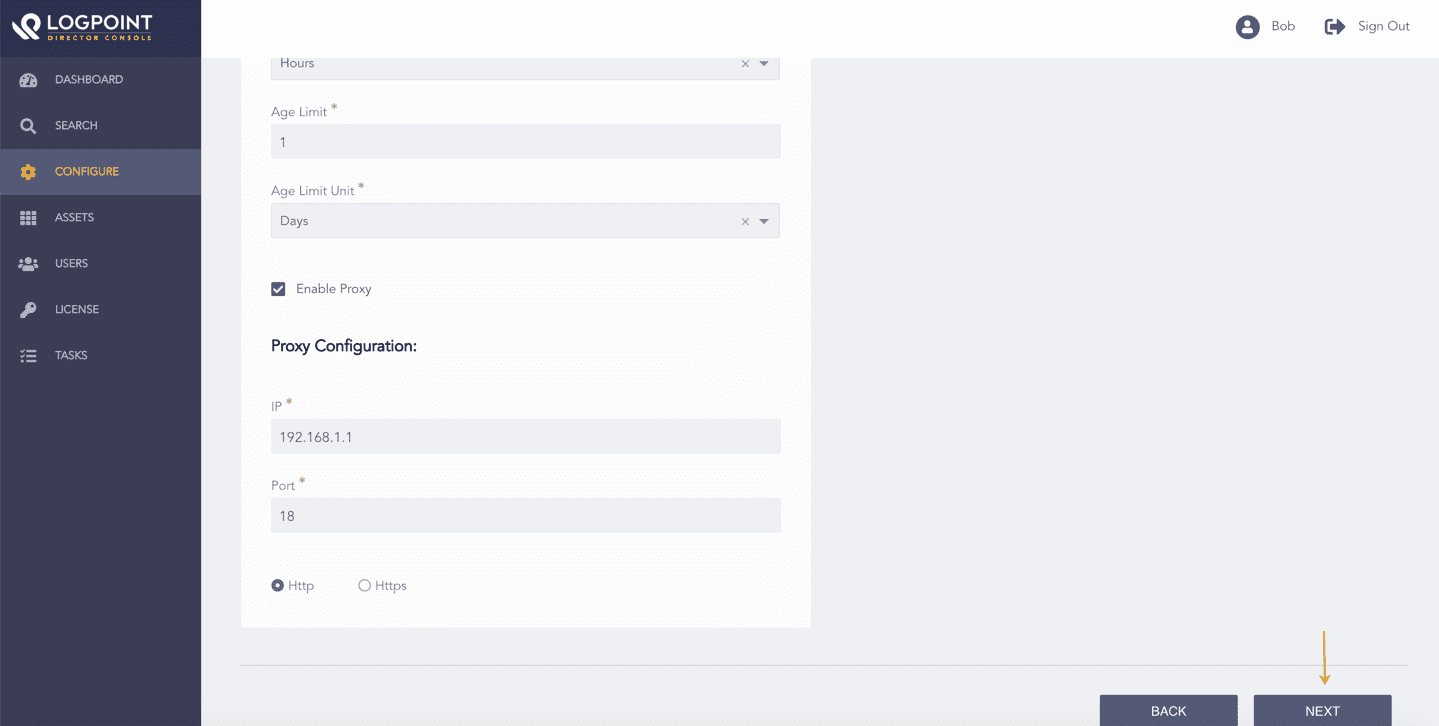
Enabling Proxy Server¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH.
Click OK.
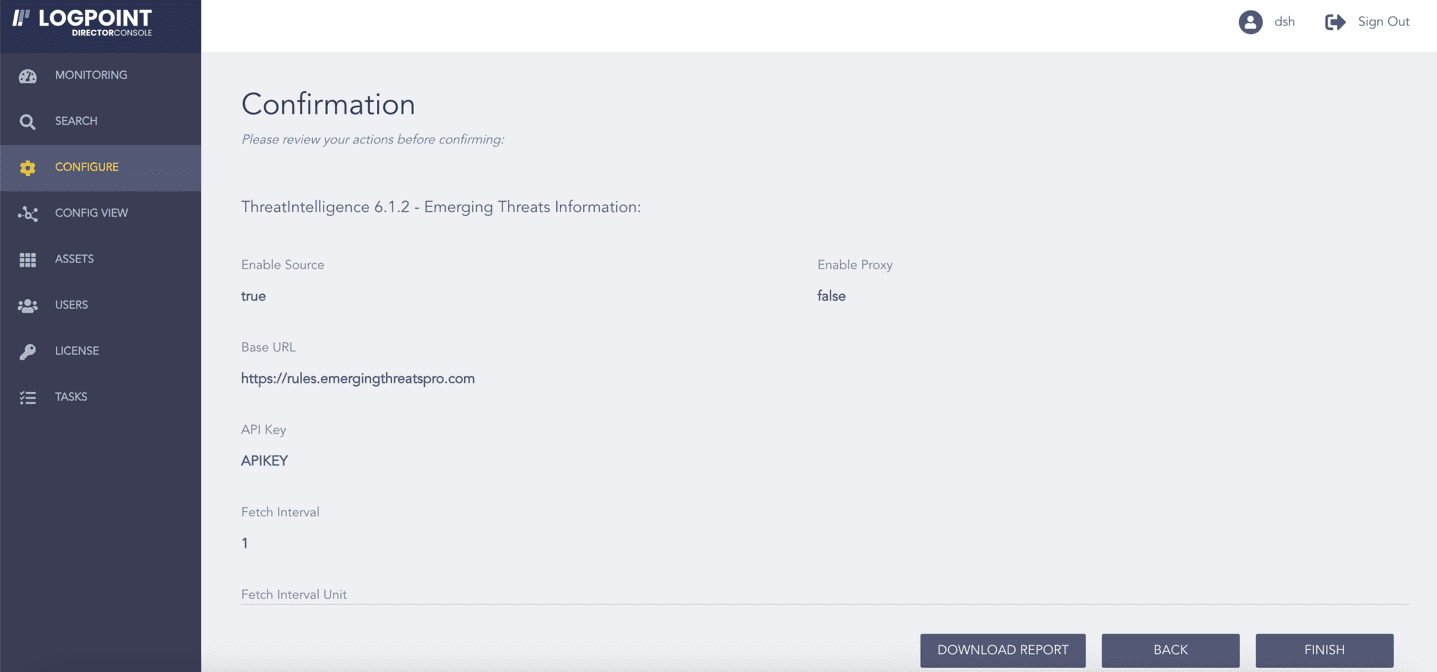
Confirming the Changes¶
Important
We will be removing the critical stack threat source from the upcoming version, so it is recommended to use the MISP threat source.
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Critical Stack API. You can select multiple Logpoints of different pools.
Select Critical Stack from the Select Plugin Sub-type drop-down.
Click NEXT.
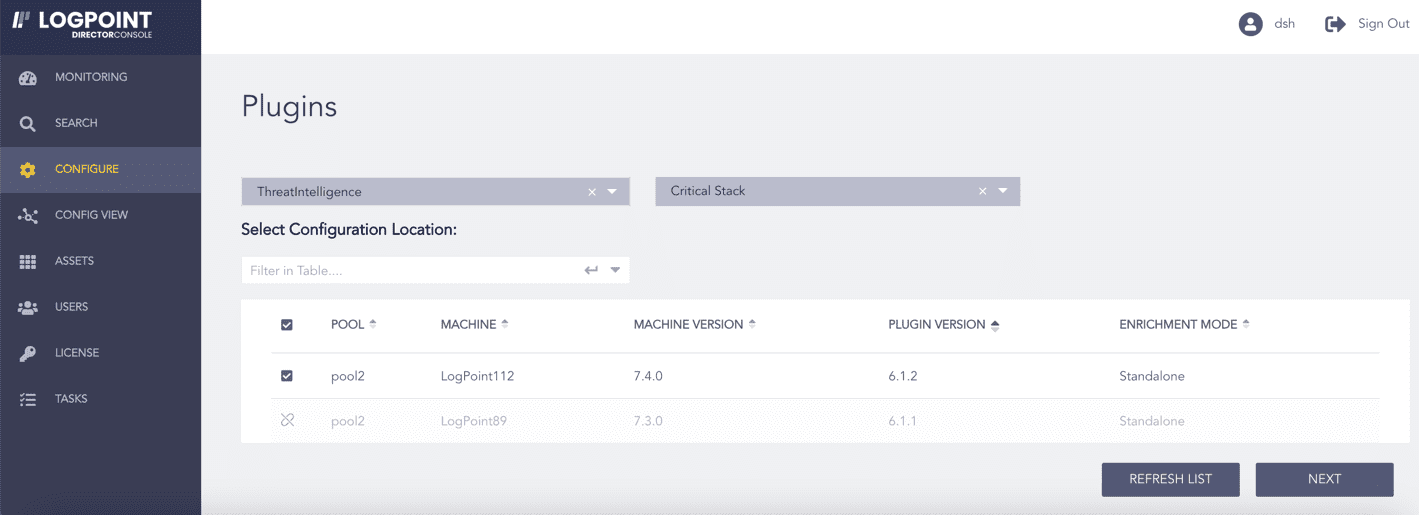
Selecting Critical Stack¶
In Create, enter the Critical Stack API Name and API Key. You can see the lists of all the Critical Stack source configurations in List.
Click NEXT.
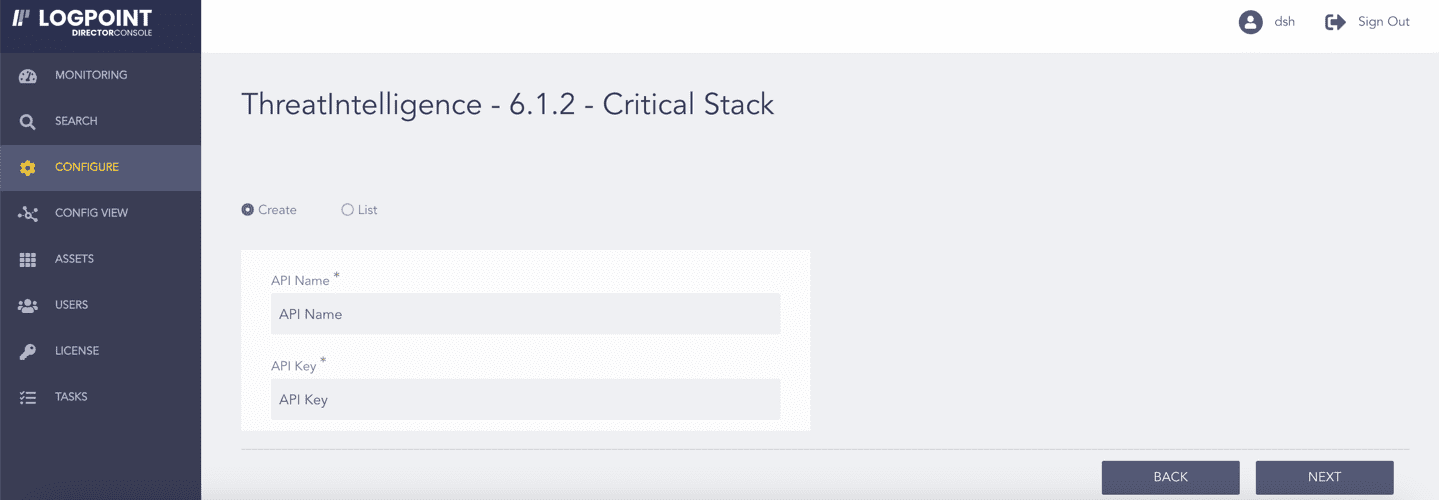
Critical Stack¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
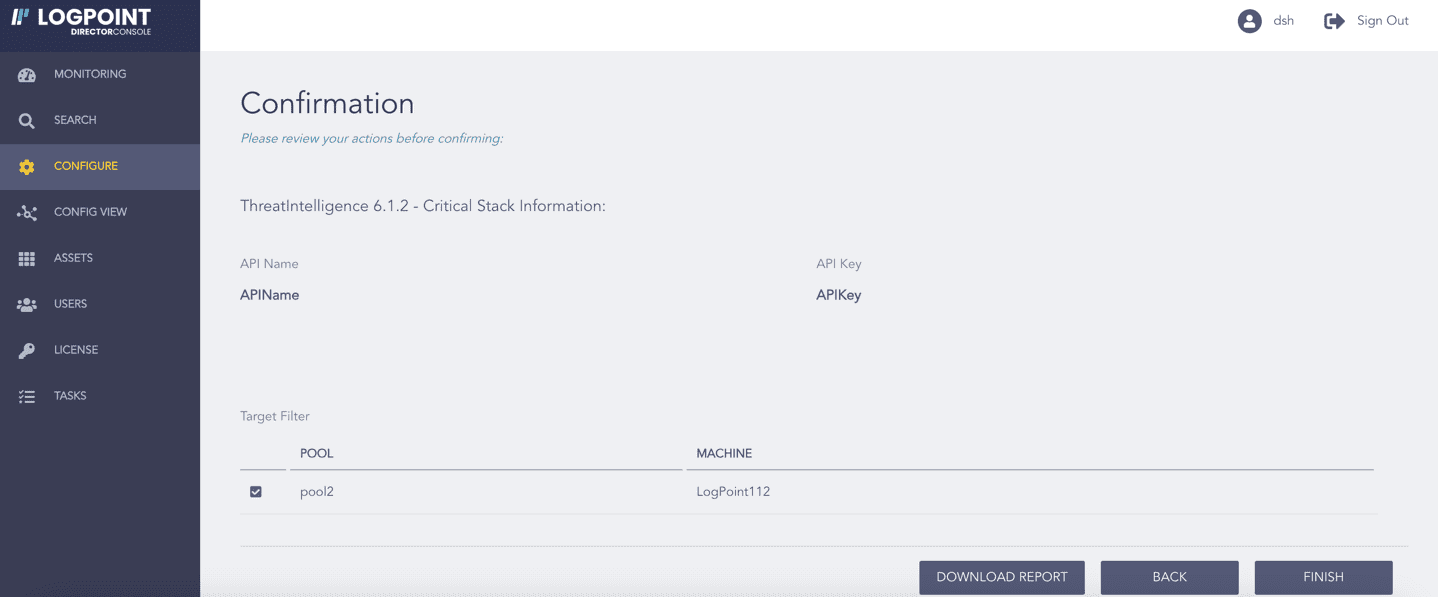
Confirming the Changes¶
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Critical Stack Source. You can select multiple Logpoints of different pools.
Select Critical Stack Settings from the Select Plugin Sub-type drop-down.
Click NEXT.
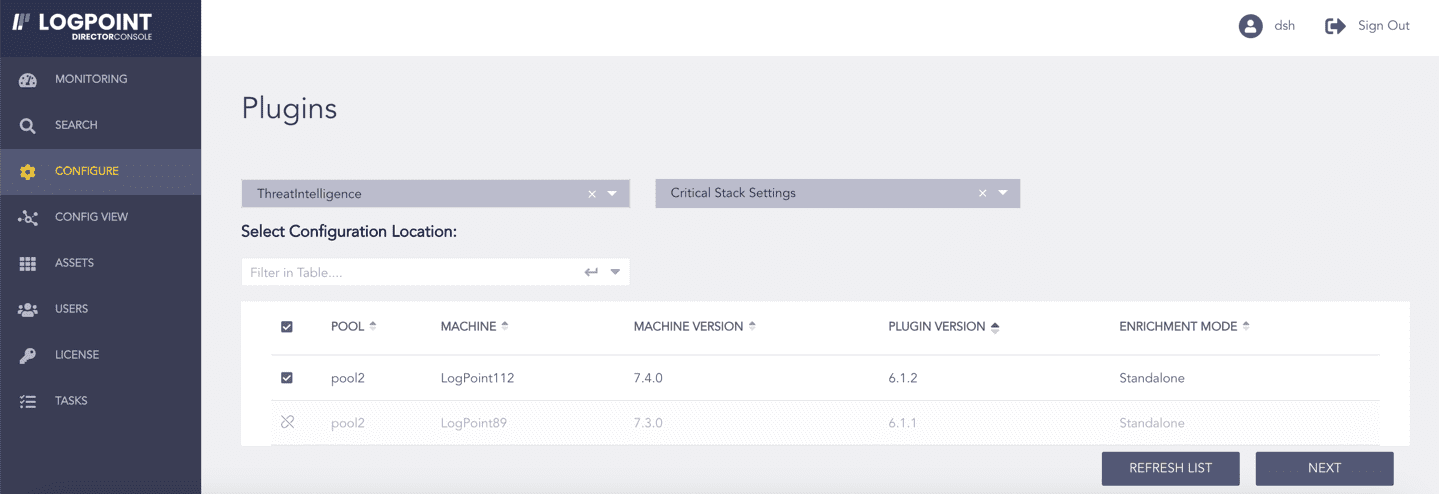
Selecting Critical Stack Settings¶
Select Enable Source to activate Critical Stack.
Enter the Fetch Interval.
Select the Fetch Interval Unit in hours or days.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select the Age Limit Unit in hours or days.
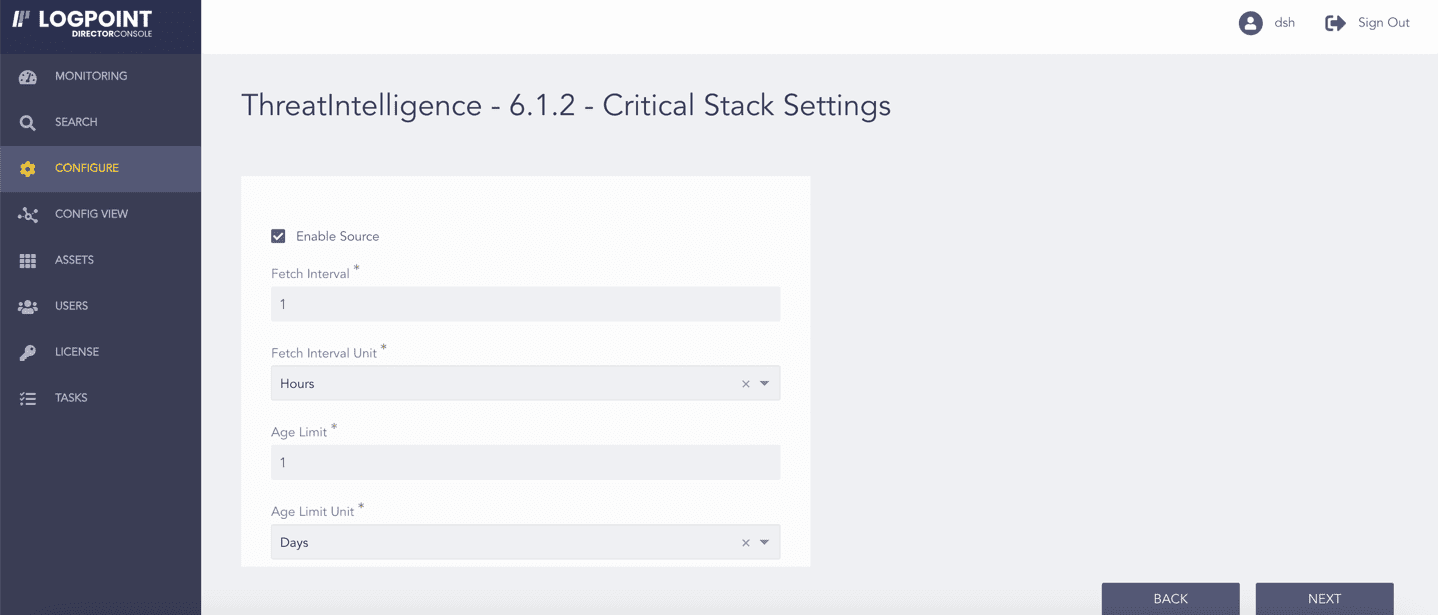
Enabling Critical Stack¶
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
13.1. Enter the proxy server IP Address and Port number.
13.2. Select either Http or Https protocol.
Click NEXT.

Enabling Proxy Server¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
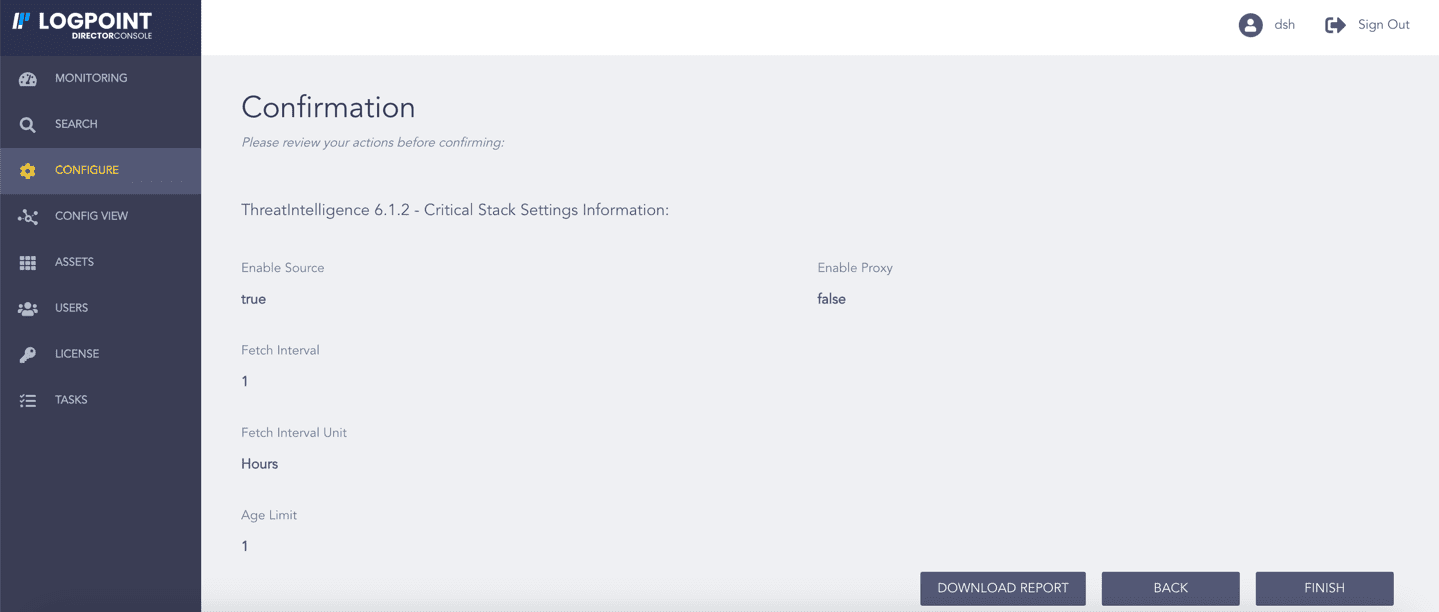
Confirming the Changes¶
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure CSIS. You can select multiple Logpoints of different pools.
Select CSIS from the Select Plugin Sub-type drop-down.
Click NEXT.
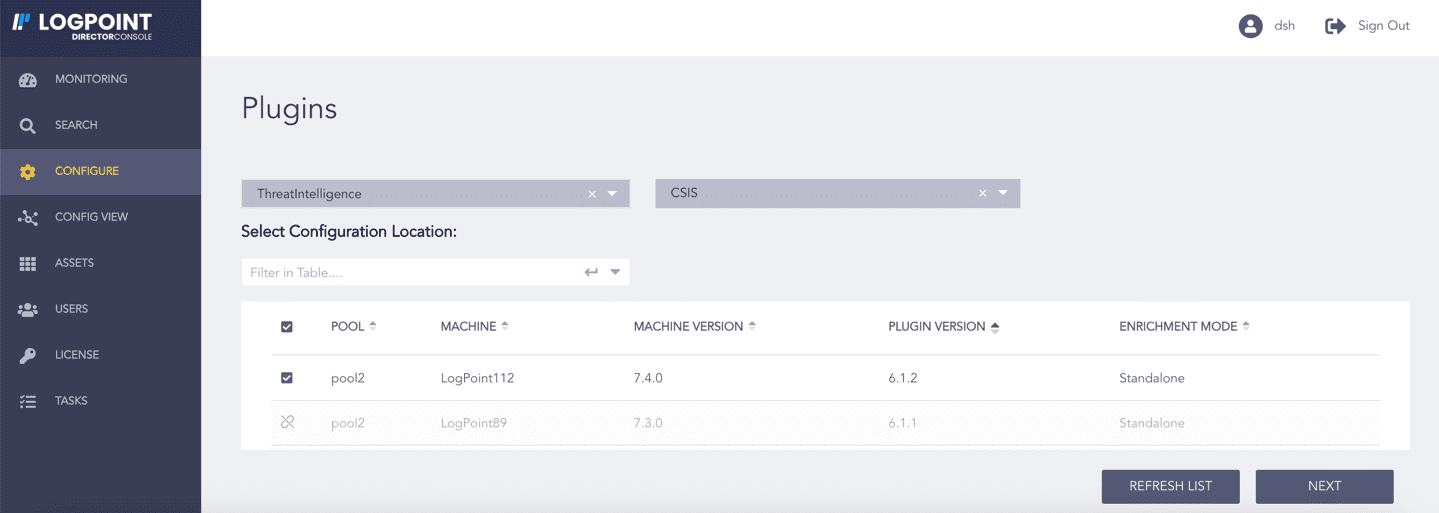
Selecting CSIS¶
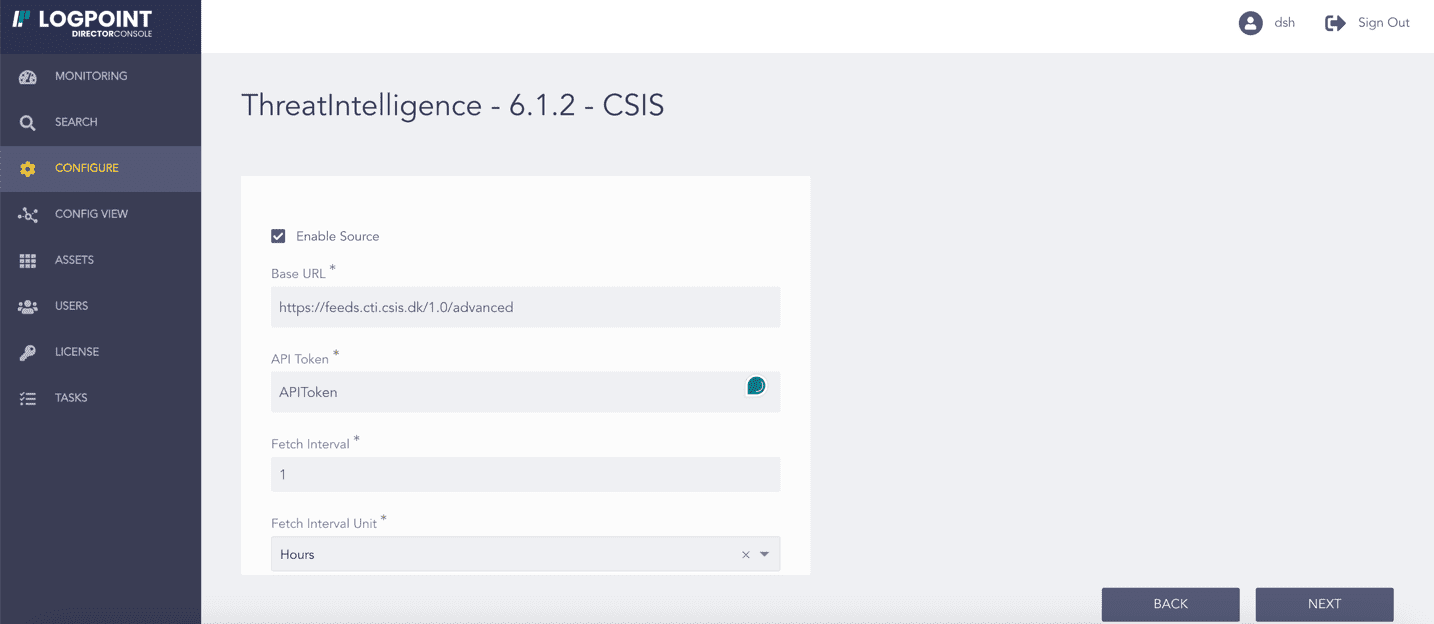
Select Enable Source to activate CSIS.
Enter the CSIS Base URL and API Token.
Enter the Fetch Interval.
Select the Fetch Interval Unit in hours or days.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select the Age Limit Unit in hours or days.
Enabling CSIS¶
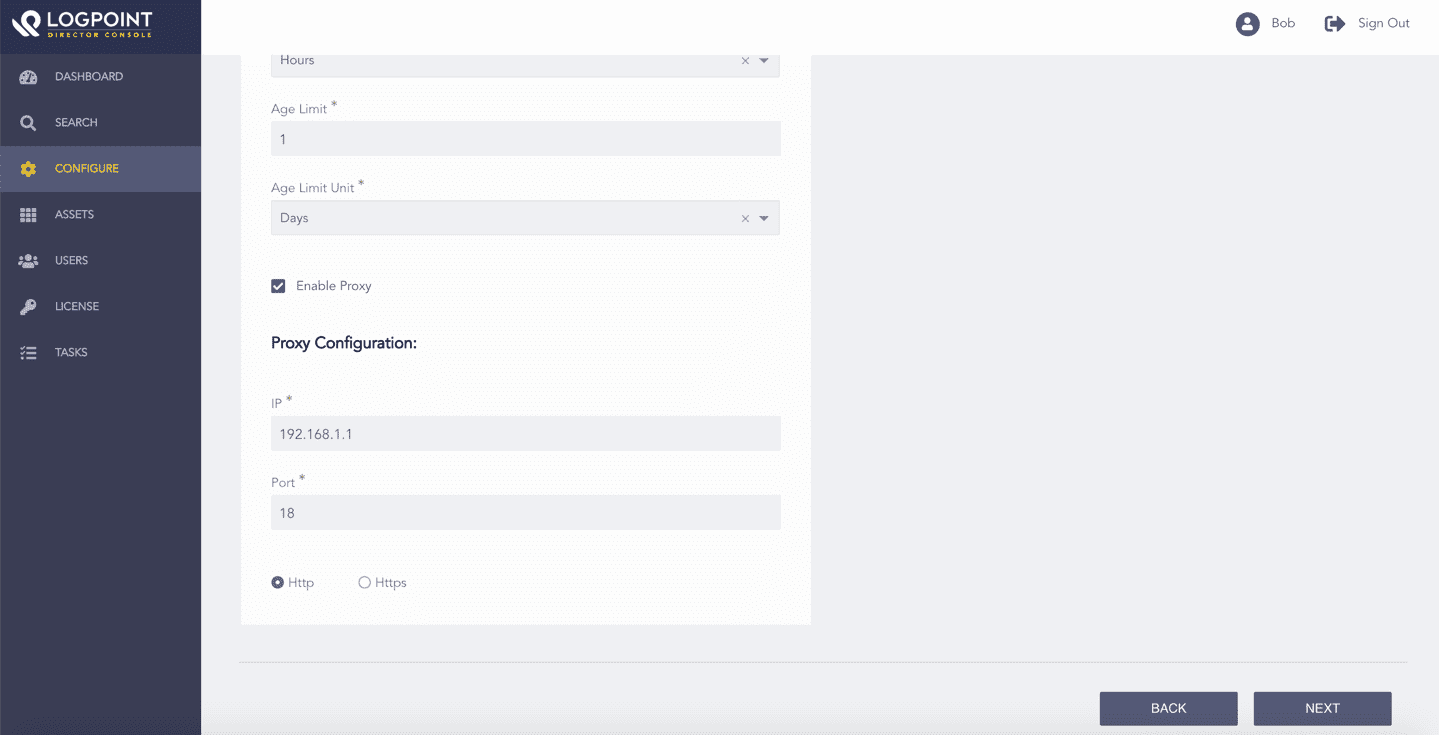
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
14.1. Enter the proxy server IP Address and Port number.
14.2. Select either Http or Https protocol.
Click NEXT.
Enabling Proxy Server¶
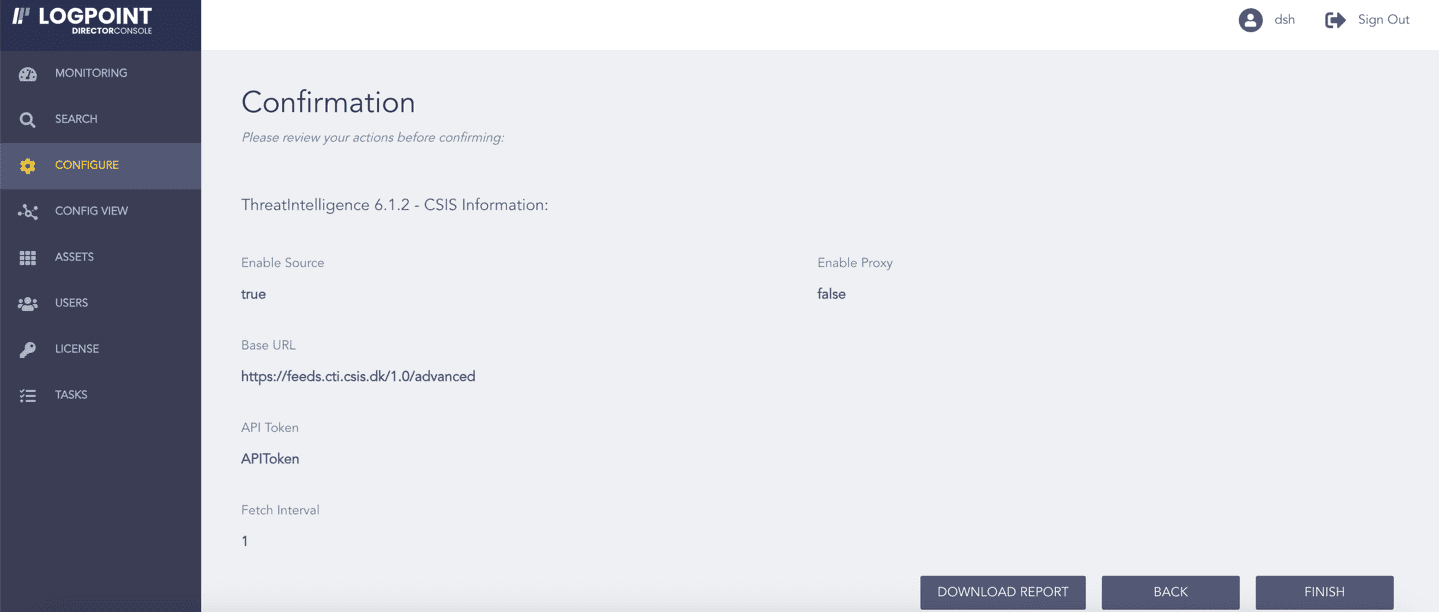
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
Confirming the Changes¶
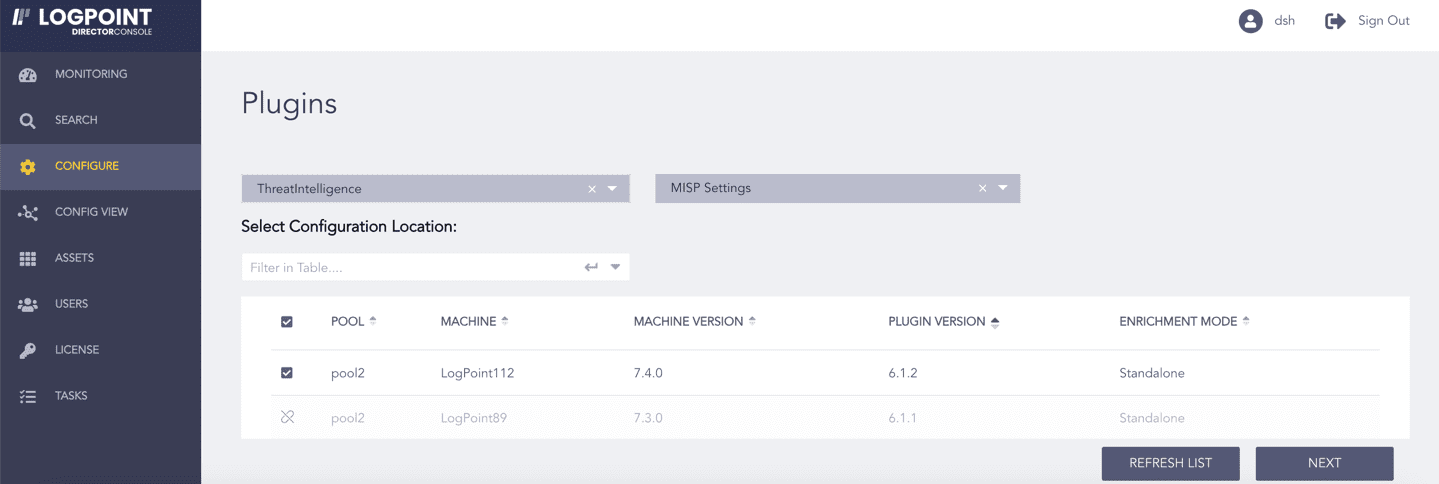
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure MISP Settings. You can select multiple Logpoints of different pools.
Select MISP Settings from the Select Plugin Sub-type drop-down.
Click NEXT.
Selecting MISP Settings¶
Select Enable Source to activate MISP.
Enter the Fetch Interval.
Select a Fetch Interval Unit.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select an Age Limit Unit.
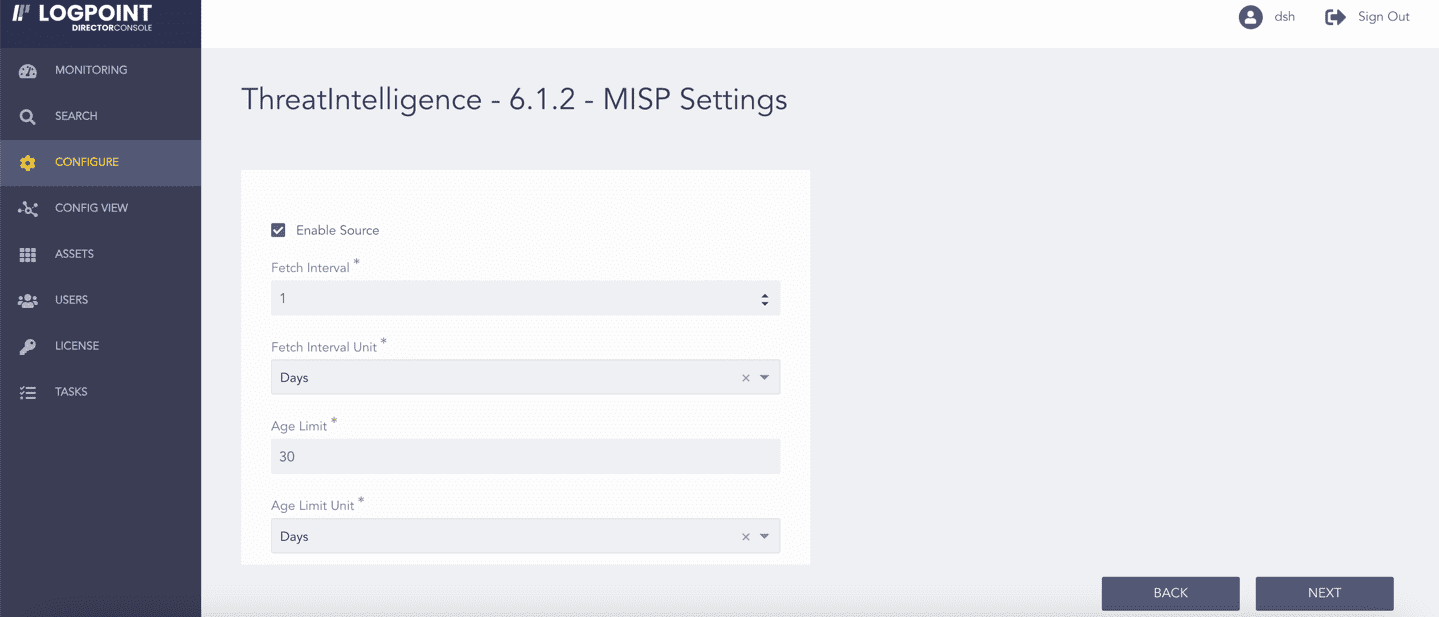
Enabling MISP¶
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
13.1. Enter the proxy server IP Address and Port number.
13.2. Select either Http or Https protocol.
Click NEXT.
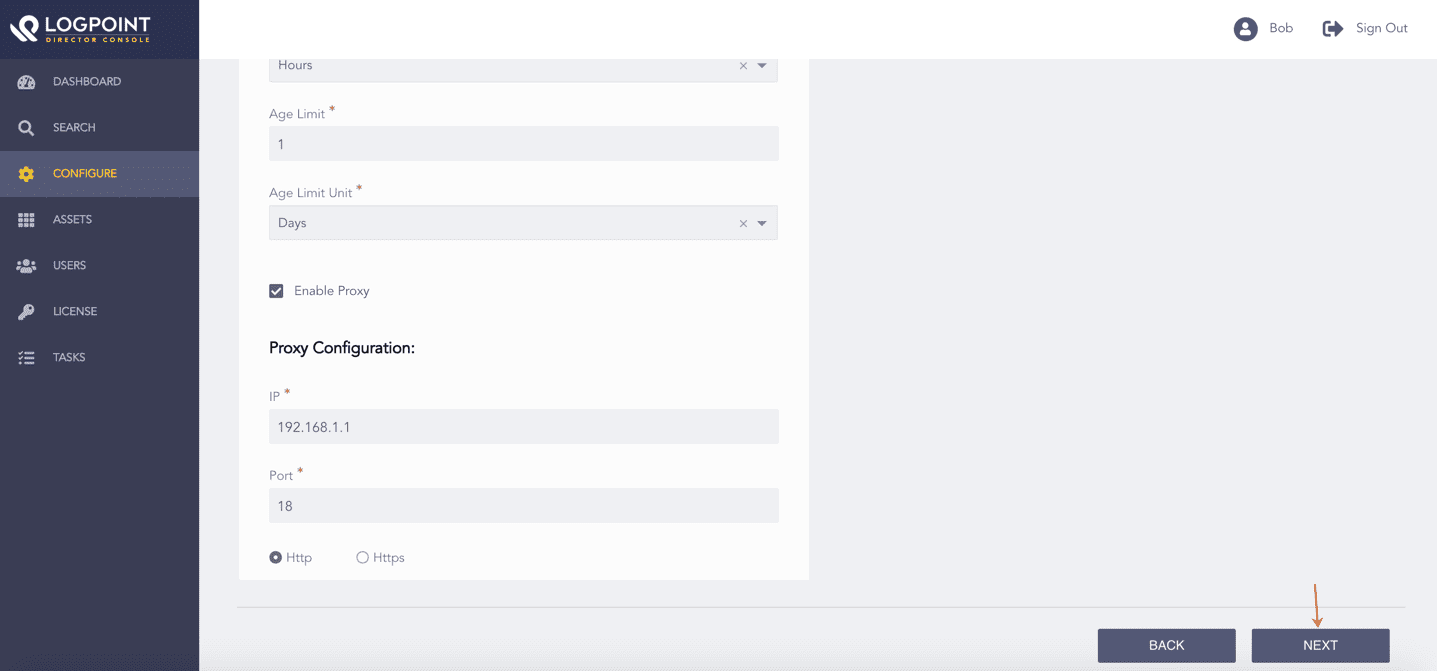
Enabling Proxy Server¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
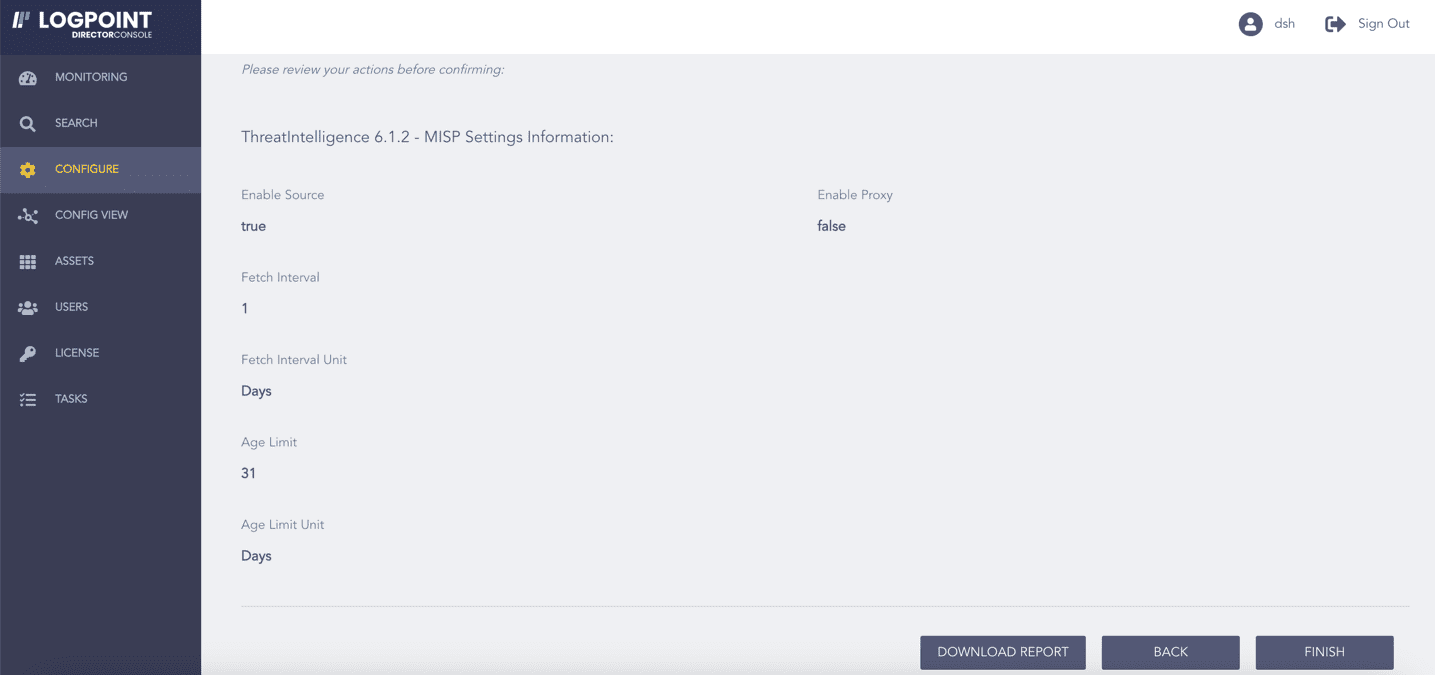
Confirming the Changes¶
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure MISP. You can select multiple Logpoints of different pools.
Select MISP from the Select Plugin Sub-type drop-down.
Click NEXT.
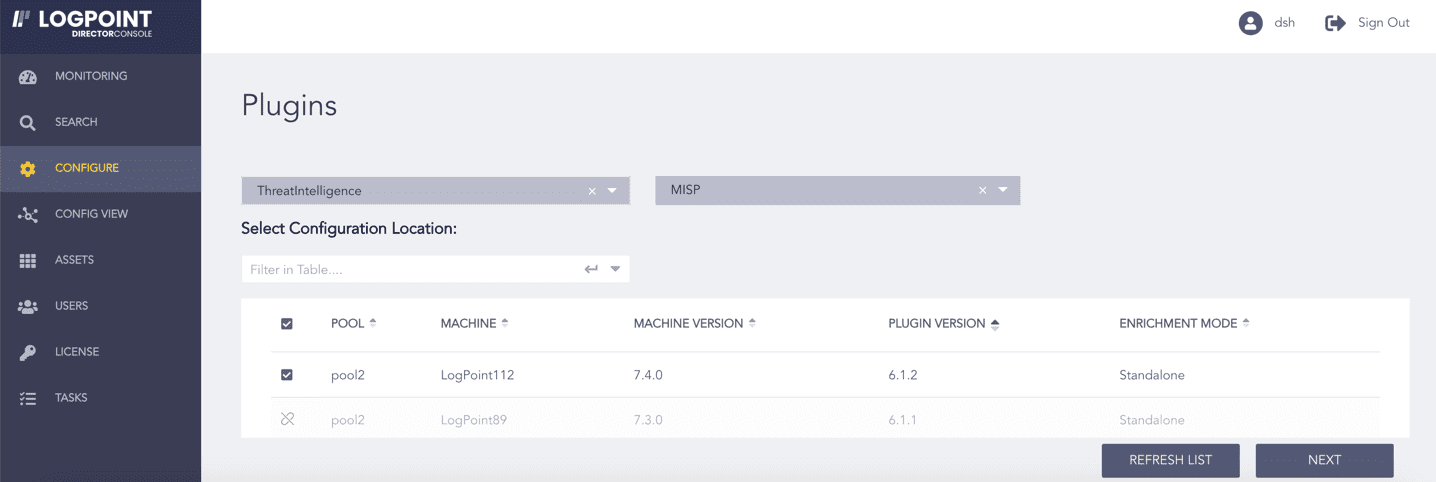
Selecting MISP¶
Select API to use an API key to fetch MISP feeds or select Free Feed to fetch free MISP feeds.
Threat Intelligence configures the Botvrij.eu free MISP feed by default. However, it is only configured if Threat Intelligence is freshly installed or if MISP is not configured while upgrading Threat Intelligence.
If API is selected:
8.1. Enter the MISP Base URL and the API Key.
8.2. Enter the MISP source parameters in a JSON format in Filter Parameter to filter incoming logs. Go to the MISP documentation for the list of parameters.
8.3. Select a date from when Threat Intelligence is to fetch logs in Logs From.
8.4. Select Verify to ensure a secure connection.
8.5. Select Upload Certificate File to use a self-signed SSL certificate.
8.6. Browse for the location of the self-signed SSL certificate and click Open.
8.7. Click Upload.
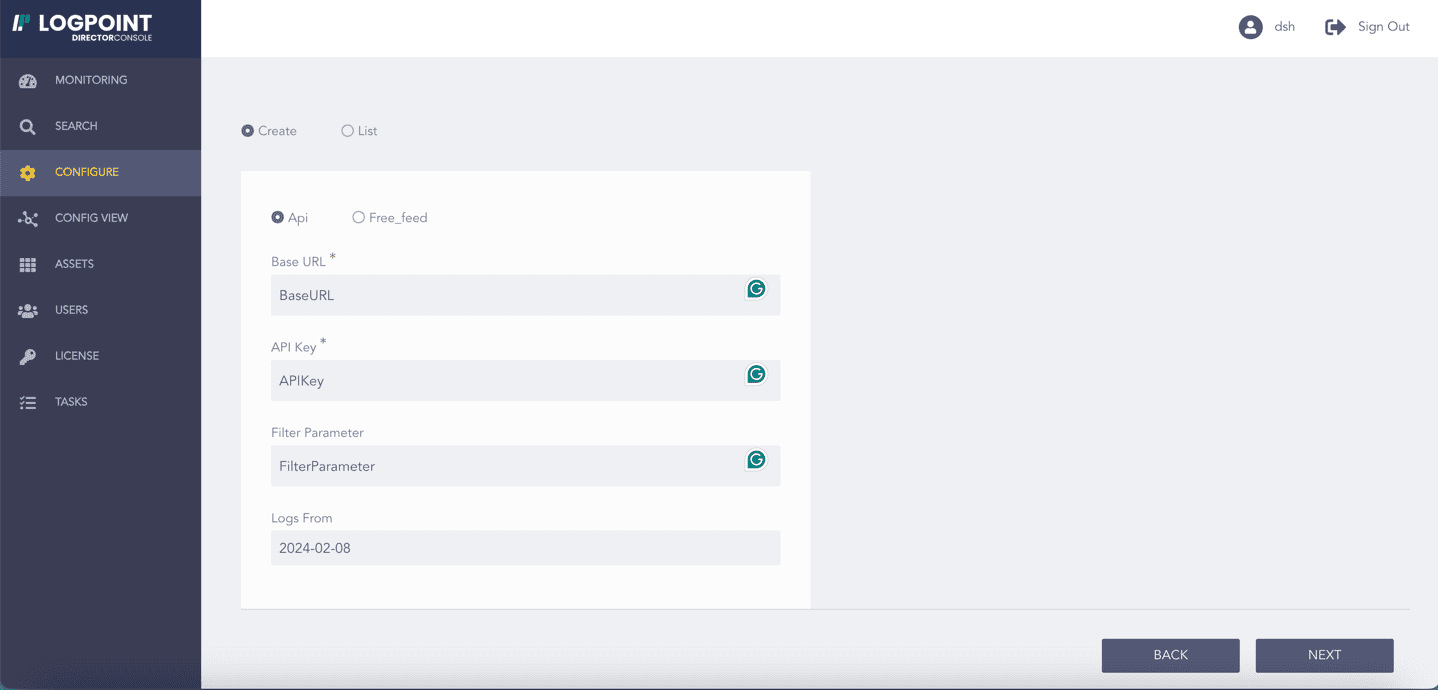
Selecting API¶
If Free Feed is selected:
9.1. Enter the MISP Base URL.
9.2. Select a date from when Threat Intelligence is to fetch logs in Logs From.
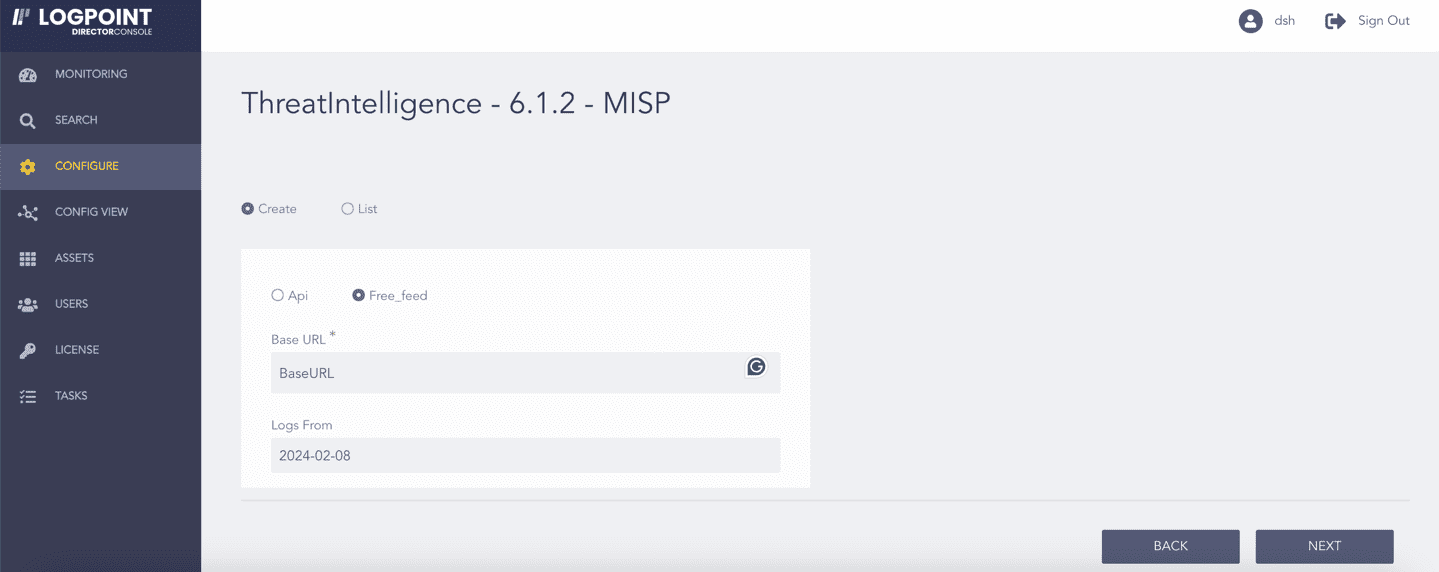
Selecting Free Feed¶
You can find the lists all the MISP configurations in List.
Click NEXT.
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
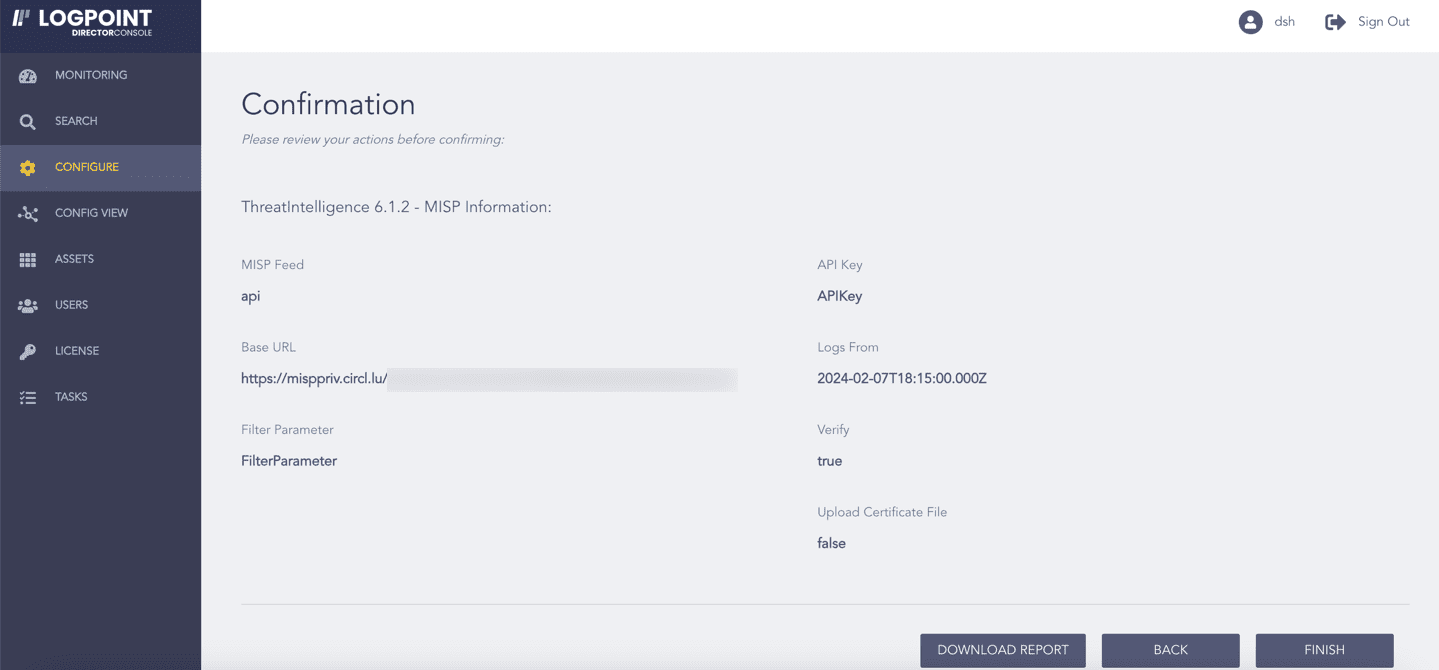
Confirming the Changes¶
Custom CSV enables you to upload a custom CSV file as a TI source. The CSV file must have the following headers:
domain, category, score, first_seen, last_seen, ports, ip, url, type, file_hashNote
The field ports is optional. You can specify multiple ports by separating it with space.
The first_seen and last_seen data fields must have the yyyy-mm-dd format.
Threat Intelligence ignores fields and their values if the CSV is not in the above format.
To configure the Custom CSV:
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Custom CSV. You can select multiple Logpoints of different pools.
Select Custom CSV from the Select Plugin Sub-type drop-down.
Click NEXT.
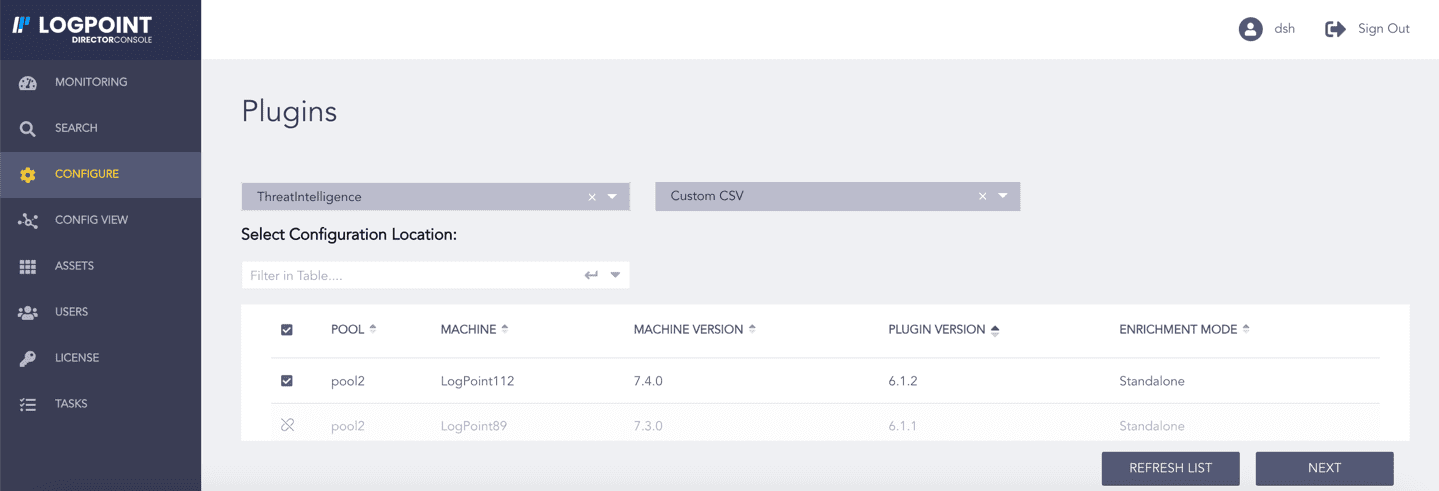
Selecting Custom CSV¶
Select Enable Source to activate custom CSV.
Enter the Base URL. It must link to the custom CSV file.
Enter the Fetch Interval.
Select the Fetch Interval Unit in hours or days.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select the Age Limit Unit in hours or days.
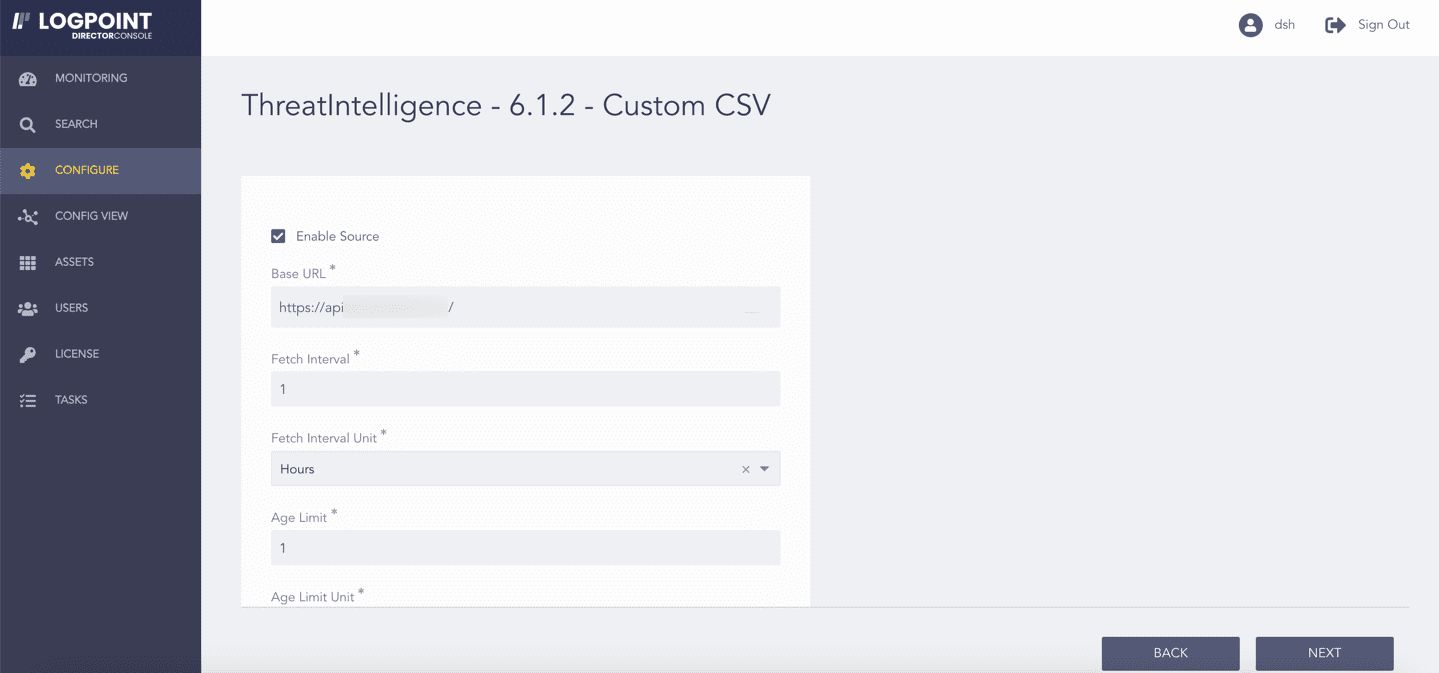
Enabling Custom CSV¶
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
14.1. Enter the proxy server IP Address and Port number.
14.2. Select either Http or Https protocol.
Click NEXT.
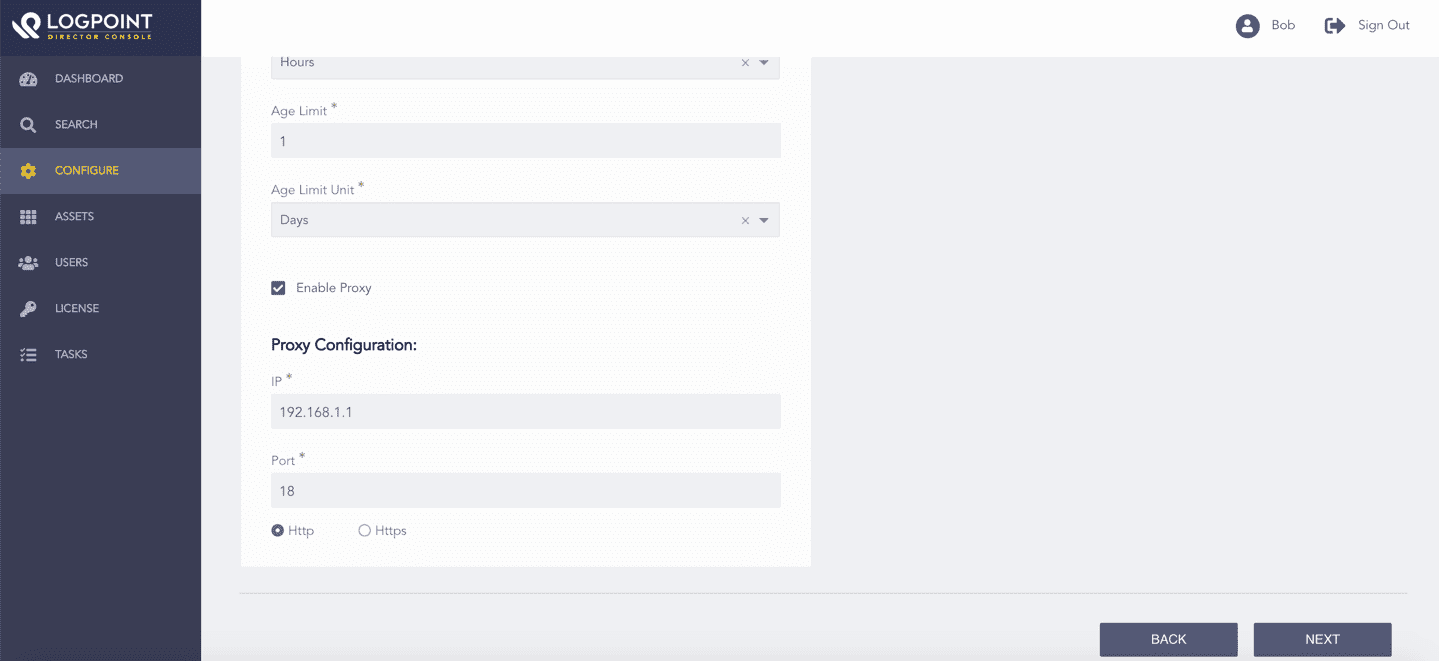
Enabling Proxy Server¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
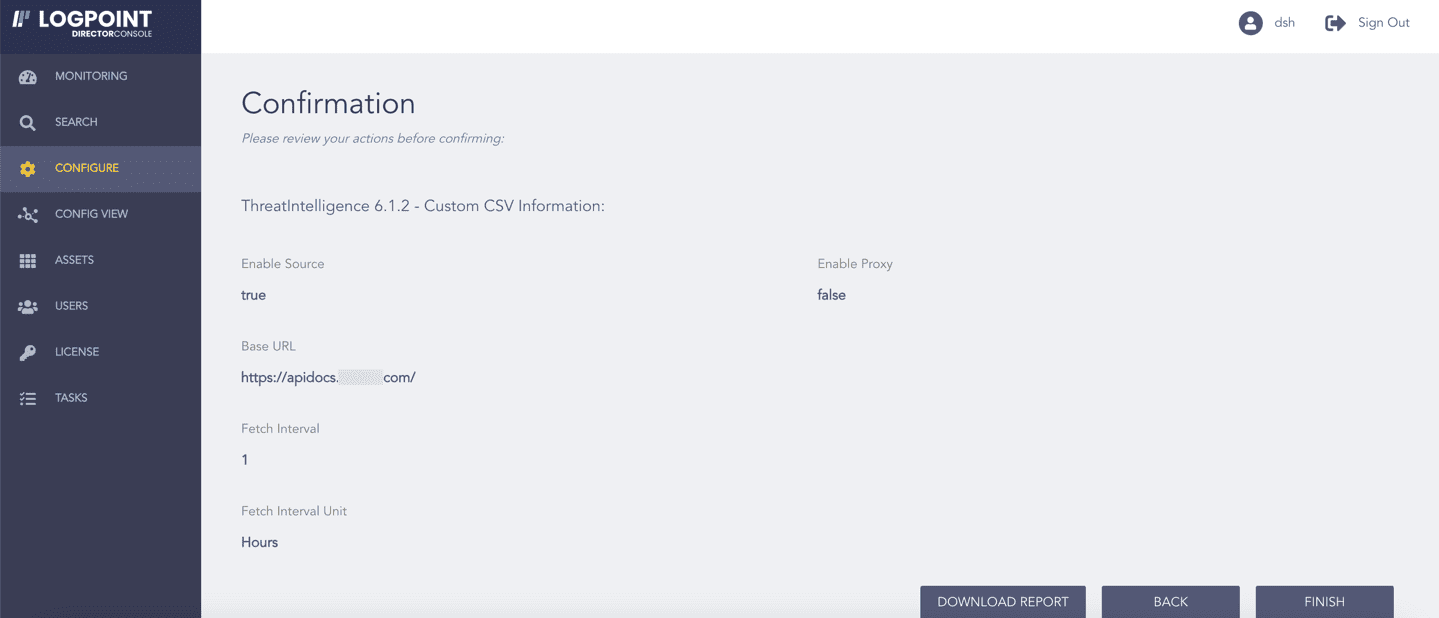
Confirming the Changes¶
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Blueliv. You can select multiple Logpoints of different pools.
Select Blue Liv from the Select Plugin Sub-type drop-down.
Click NEXT.
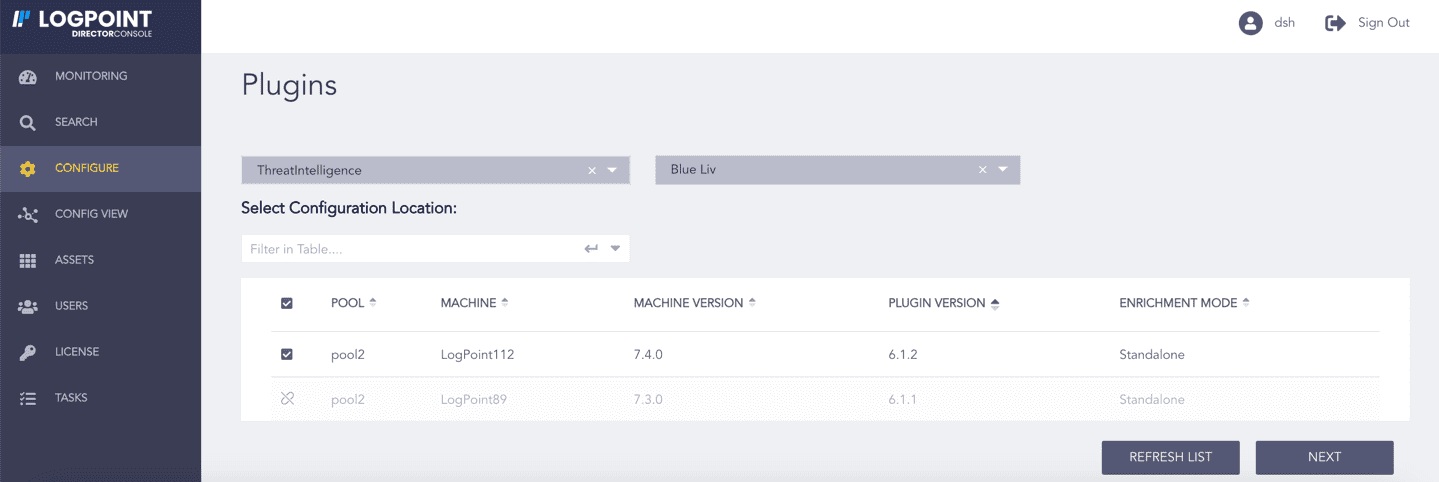
Selecting Blue Liv¶
Select Enable Source to activate Blue Liv.
Enter the Blueliv Base URL and API Key.
Enter the Fetch Interval.
Select the Fetch Interval Unit in hours or days.
Enter the Age Limit, which is the retention period of the fetched data in days or hours. Enter it as 0 to retain the last fetched data until the next successful fetch.
Select the Age Limit Unit in hours or days.
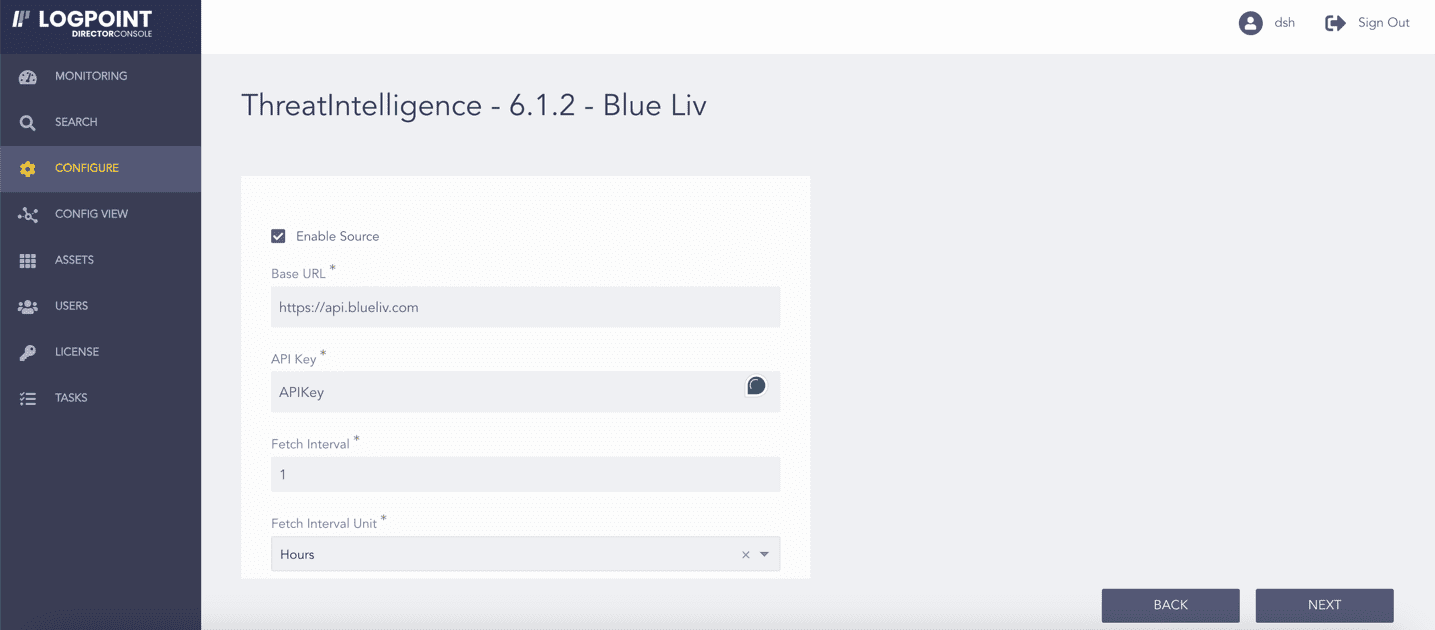
Enabling Blue Liv¶
Select Enable Proxy to use a proxy server.
In Proxy Configuration:
14.1. Enter the proxy server IP Address and Port number.
14.2. Select either Http or Https protocol.
Click NEXT.
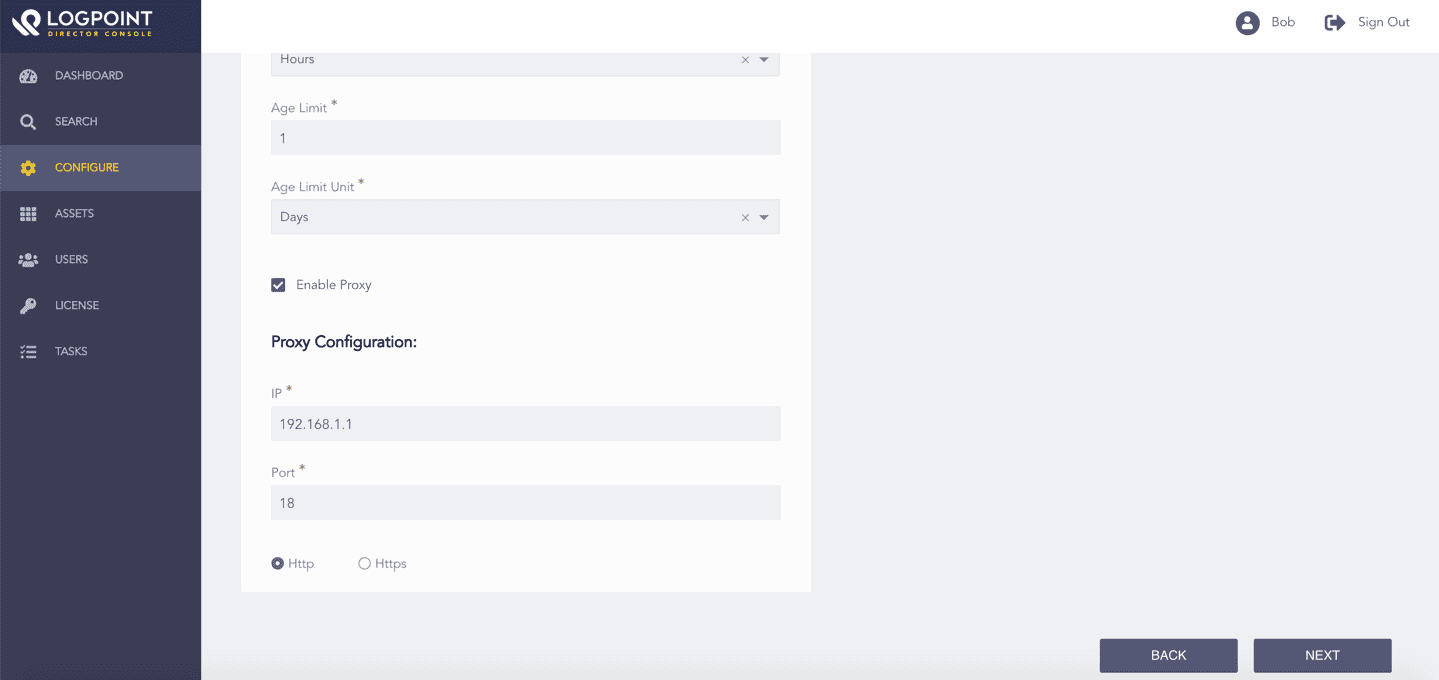
Enabling Proxy Server¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
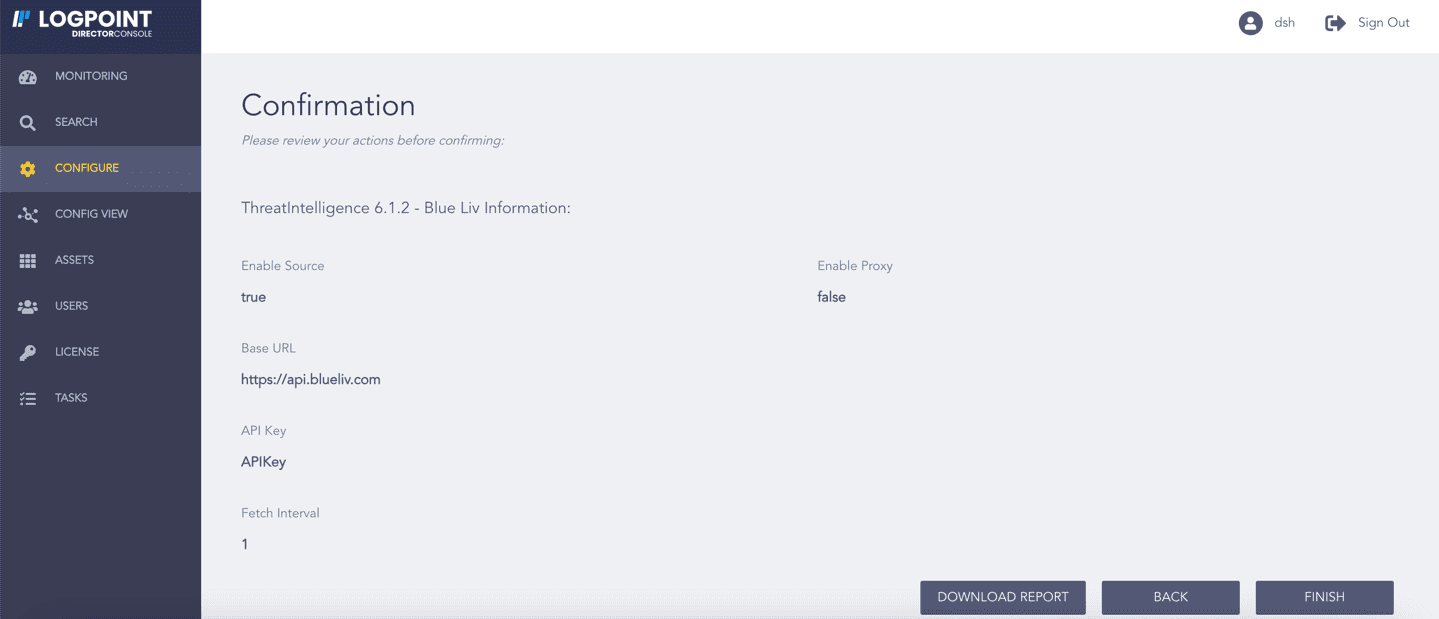
Confirming the Changes¶
Mapping enables you to standardize logs by assigning the fields of fetched logs to the fields of the Logpoint Threat Intelligence Taxonomy. Threat Intelligence initially validates if you have mapped the field of a search query. If you have not mapped the field, Threat Intelligence searches the column with the same field name and enriches the logs.
The following fields are mapped by default:
source_address to ip_address
destination_address to ip_address
To map:
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Mapping. You can select multiple Logpoints of different pools.
Select Mapping from the Select Plugin Sub-type drop-down.
Click NEXT.
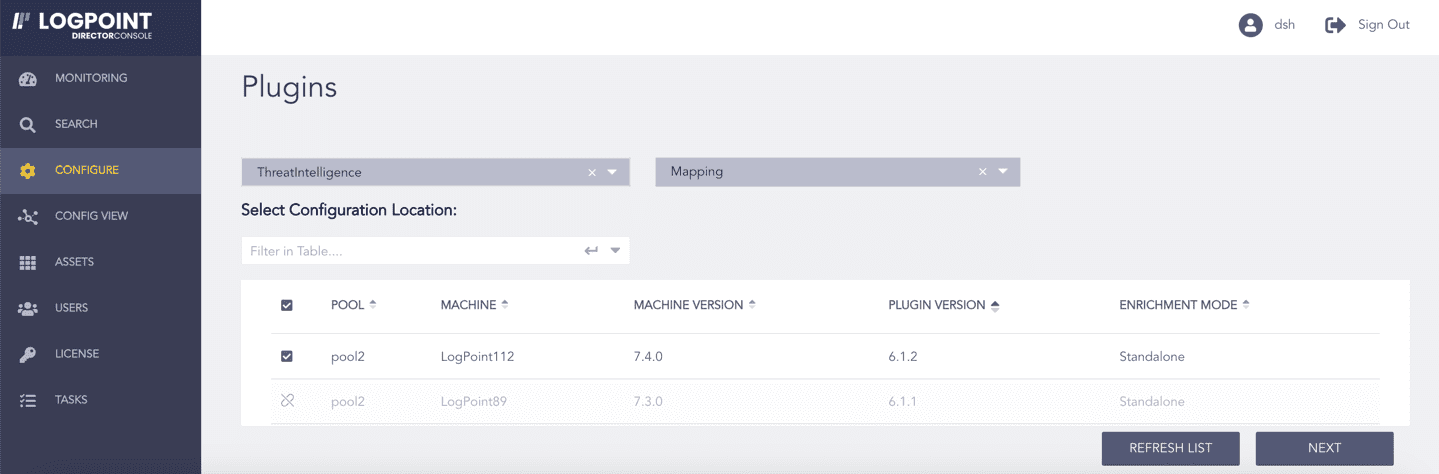
Selecting Mapping¶
In Create:
7.1. Enter the Key from the incoming log to map.
7.2. Enter the Column name from the Logpoint taxonomy to map the key.
You can find all the mapping configurations in List.
Click NEXT.
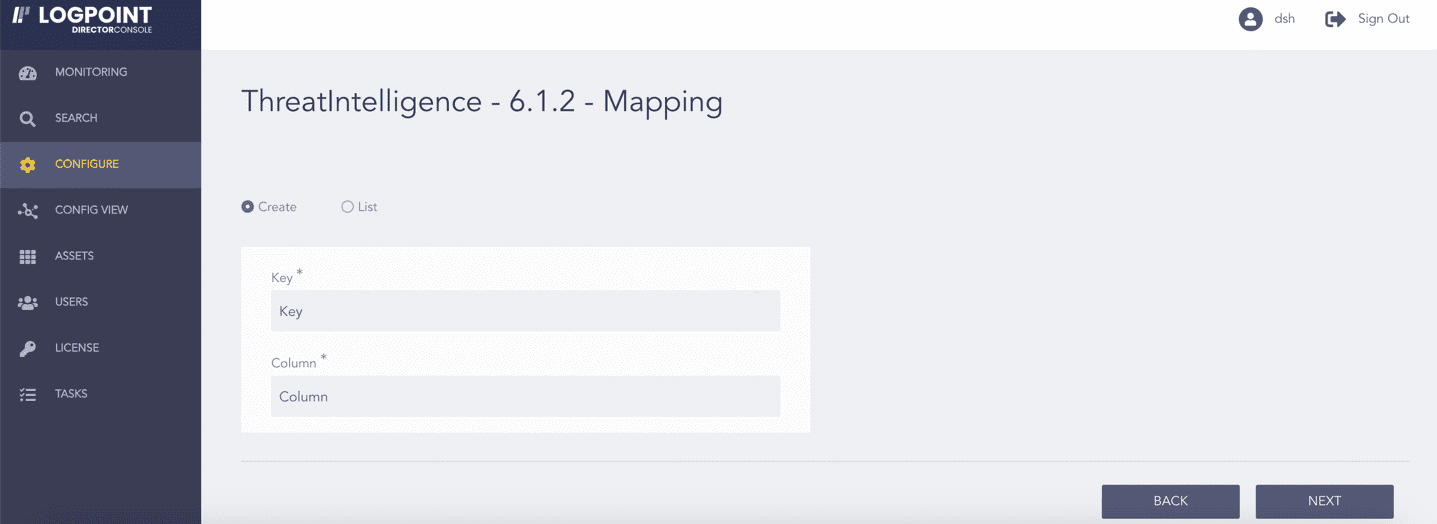
Mapping¶
Review your changes. You can go BACK to make any changes if necessary.
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
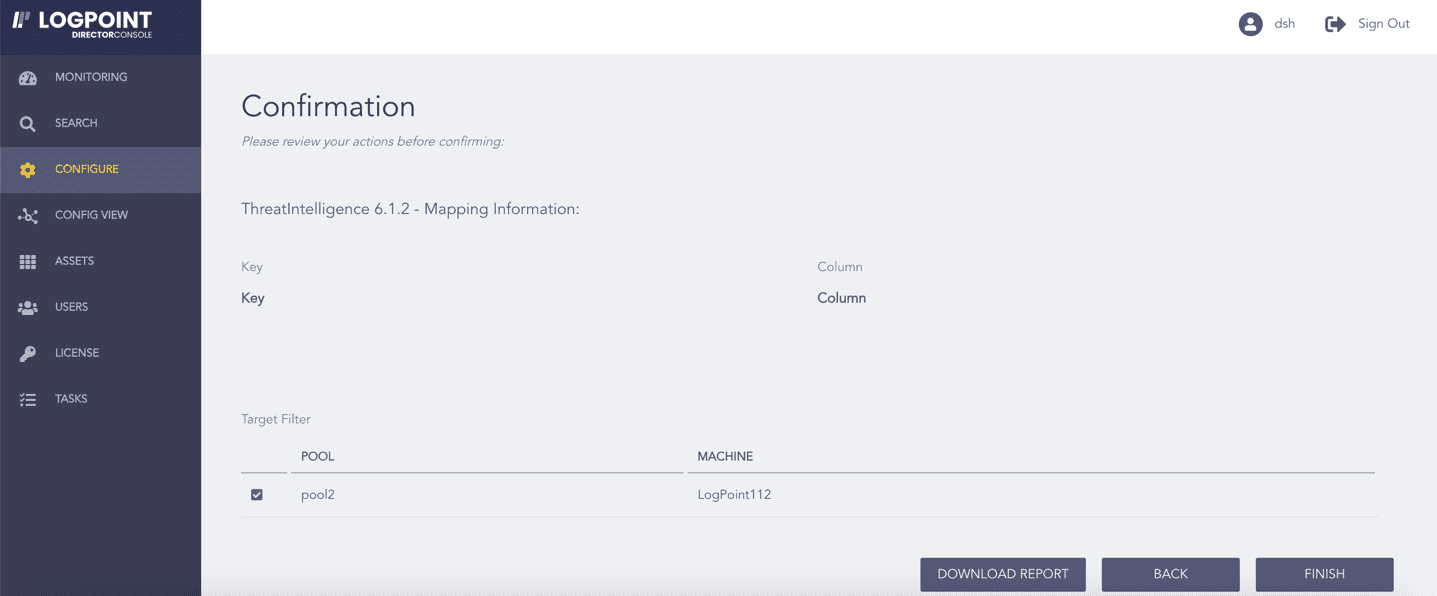
Confirming the Changes¶
Alias enables you to assign a pseudoname to one or multiple field names of the incoming log.
To assign an alias:
Click Configure in the navigation bar.
Under Settings, click Plugins.
Select ThreatIntelligence from the Select Plugin Type drop-down.
Select the Logpoint to configure Alias. You can select multiple Logpoints of different pools.
Select Alias from the Select Plugin Sub-type drop-down.
Click NEXT.
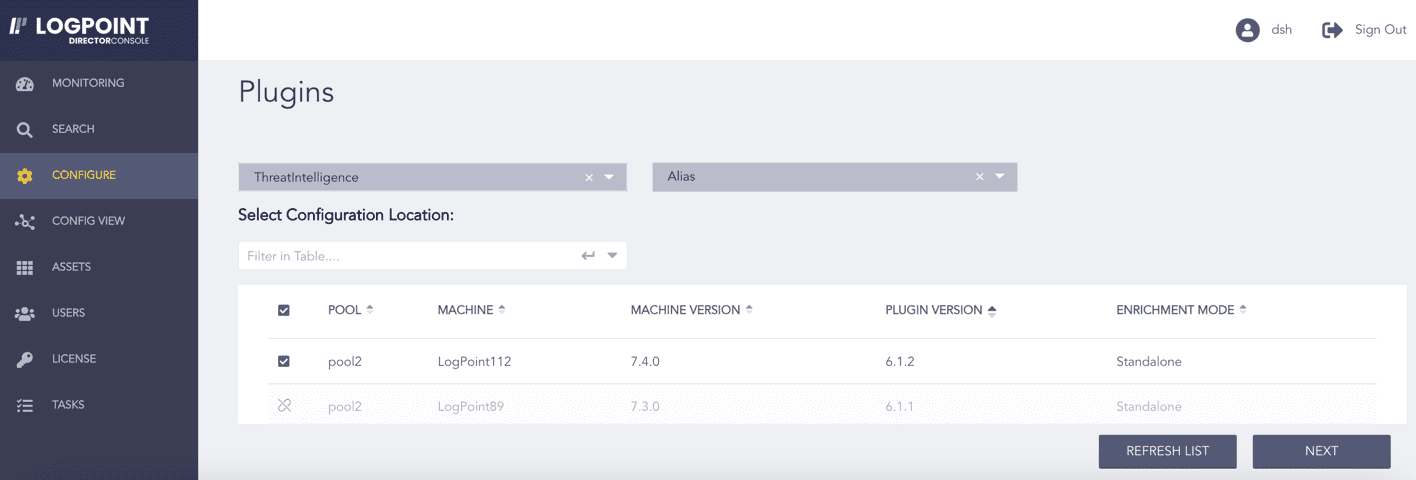
Selecting Alias¶
In Create:
7.1 Enter the Alias name.
7.2 Enter the name of one or more Fields to which the alias needs to refer.
Select a mode of display:
8.1. Select All to display both the matched and the unmatched logs. However, only the matched logs are enriched.
8.2. Select Filter to display only the matched logs.
You can find all the alias configurations in List.
Click NEXT.
Review your changes. You can go BACK to make any changes if necessary.
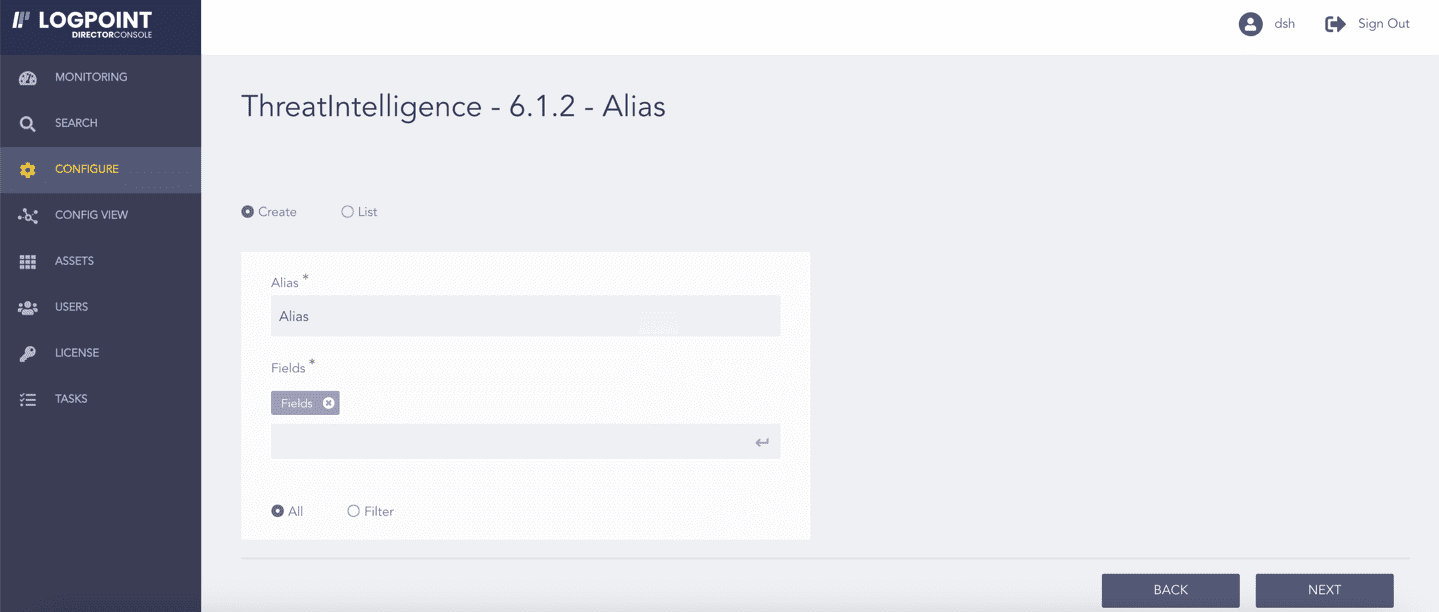
Configuring Alias¶
Note
Click Download Report to get a summary as a PDF.
Click FINISH. Click OK to confirm.
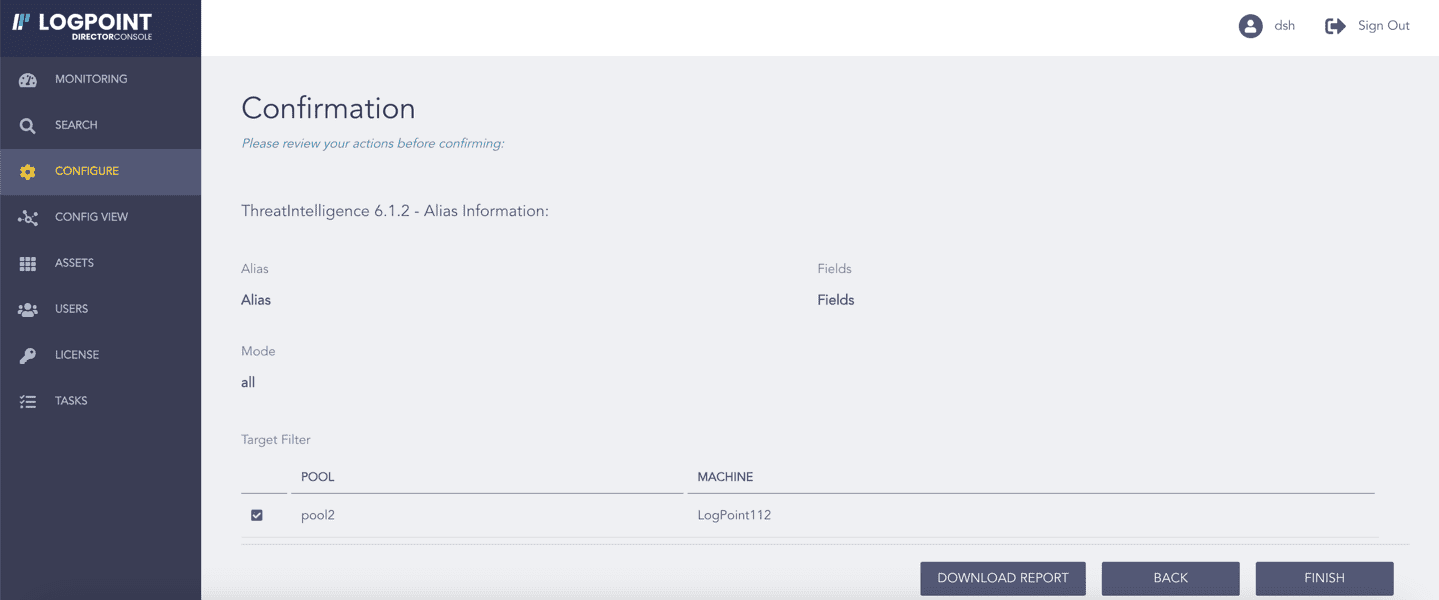
Confirming the Changes¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support